Invisible Wallet Architecture
Enterprise-grade security for your invisible wallets
Security is paramount for Shinami's invisible wallet solution. This section details how we manage that responsibility and how it relates to interacting with the Invisible Wallet API.
Key Management
Keys are used for wallet creation and transaction signing. Each wallet key pair is independently generated by the Shinami Key Service upon request from your app. They are not hierarchical and there’s no “root key.” These wallet keys are under shared custody of your app and Shinami, in that both parties will need to come together in order to sign transactions.
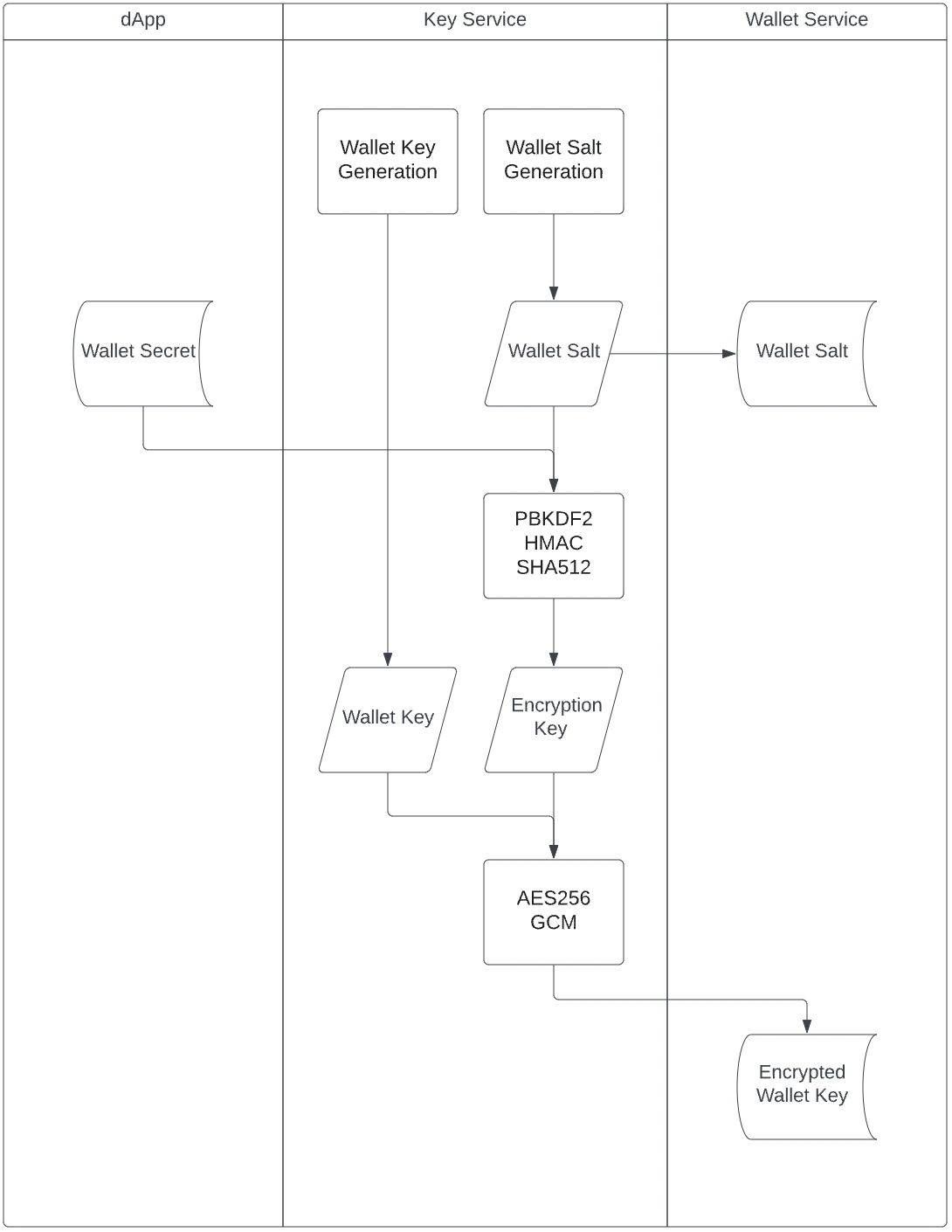
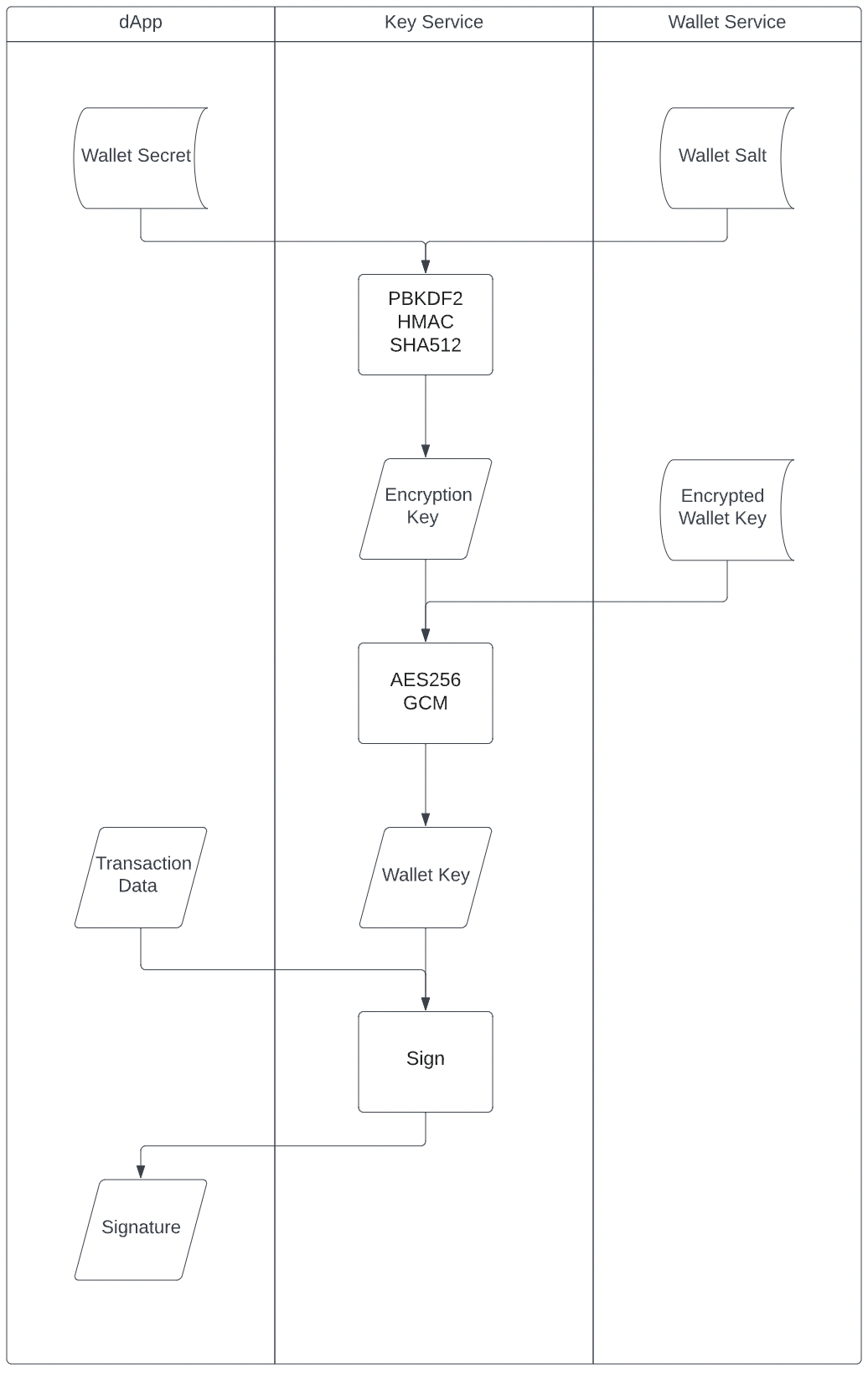
Each wallet key is recoverable from three pieces of data:
- Wallet secret - managed by the app (you)
- Wallet salt - managed by Shinami
- Encrypted wallet key - managed by Shinami
At rest, neither party has access to all three pieces. For security isolation, the Shinami side is split into two proprietary services: Shinami Key Service and Shinami Wallet Service. The following two data flow charts show who is exposed to which pieces of data. Notably, the Shinami Key Service is a compute-only service with no state persistence. It has strict input / output policies where secret materials are never leaked outside.
Key Generation Data Flow
Transaction Signing Data Flow
Note:
With this separation, it is possible for the Shinami Key Service to be hosted by the app or an independent 3rd party. This provides a trustless guarantee that all parties remain zero-knowledge of the actual wallet keys at all times.
End-to-end API Interactions
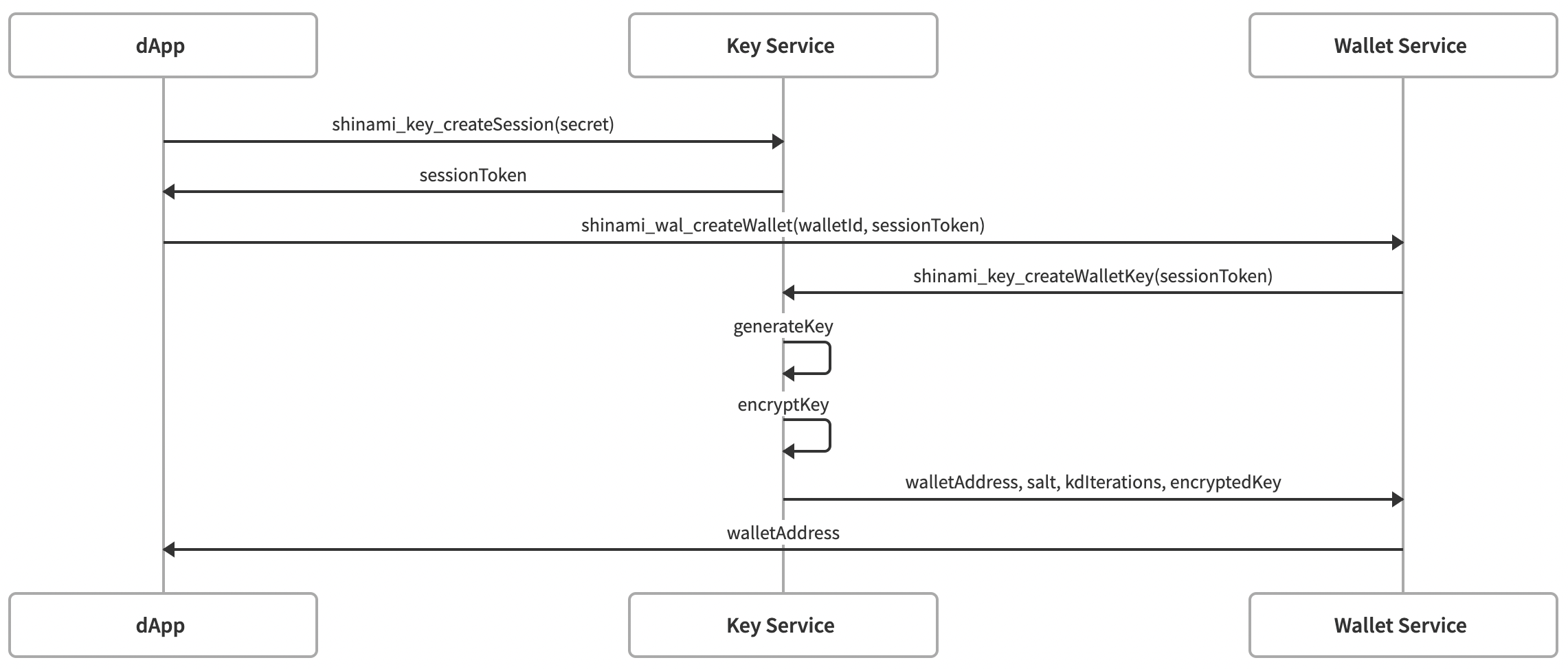
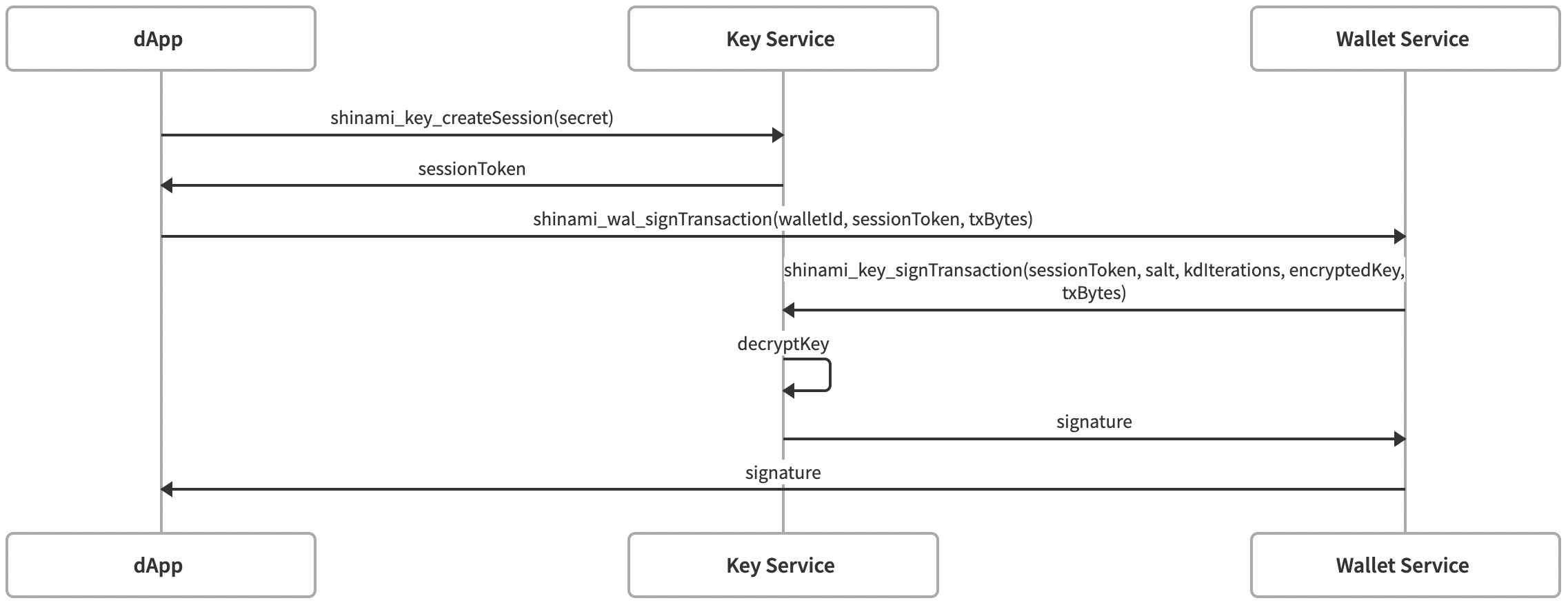
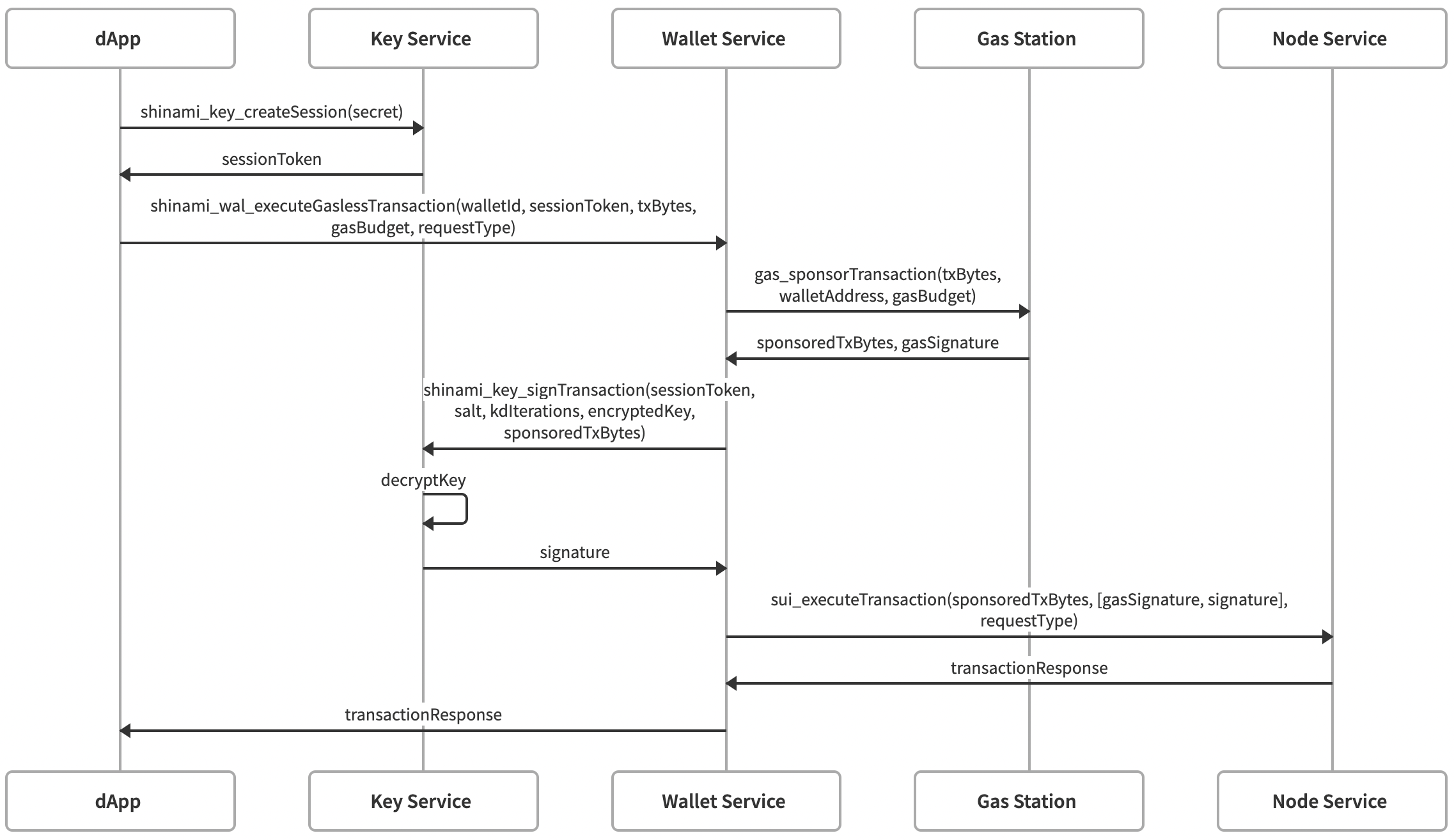
The three diagrams below further detail the interaction between your app, the Shinami Key Service and Shinami Wallet Service when using the Invisible Wallet API.
Wallet Creation
Transaction Signing
Gasless Transaction Execution
Updated 11 days ago
